TCP/IP Model
When heterogeneous devices such as computers, smartphones, embedded systems etc communicate over a network, there must be some common protocols to understand each other and exchange data. These include a set of rules that ensure the devices interpret the data consistently, can send and receive messages, and address concerns such as data formatting, error checking, routing, and reliable delivery. The rules, which govern how data is transmitted and received across the network, are known as networking protocols. A networking protocol suite refers to a collection of protocols that work together to facilitate communication between devices. The TCP/IP model is one of the most widely used protocol suites, enabling communication over the internet and other networks. It defines how data is transmitted, routed, and received, standardizing the entire communication process. The TCP/IP model is structured into four different layers, each responsible for specific tasks, and these layers collaborate to ensure end-to-end communication. The different layers in TCP/IP protocol suite are as follows:
- Application Layer
- Transport Layer
- Internet Layer
- Link Layer
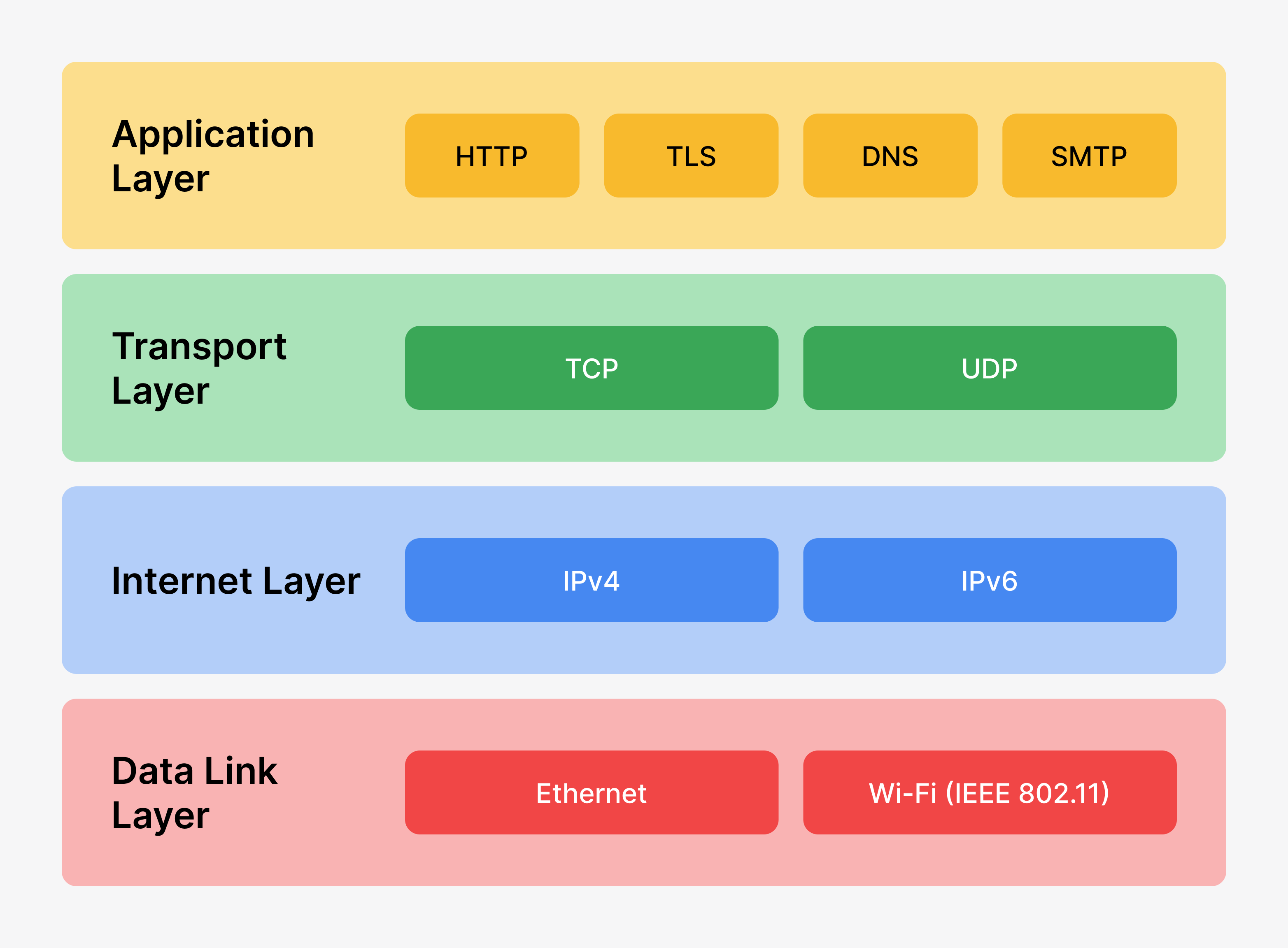
As we move from the lower layers (like the Link and Internet layers) to the higher layers (like the Transport and Application layers) in the TCP/IP model, the reliance on hardware decreases, and software implementations take over more of the responsibilities. A brief introduction to each of the layers in the TCP/IP suite is given below.
Application Layer
The Application Layer is the uppermost layer of the TCP/IP model and acts as an interface between end-user applications and the underlying lower layers. This layer includes protocols such as HTTP, FTP, SMTP, and DNS, which define how application programs (e.g., web browsers and email clients) interact with the network. These protocols allow application program users to perform activities such as web browsing, file transfer, email communication, and domain name resolution. Application layer is also responsible for data formatting which is the process of converting and structuring data into a format that can be understood by both the sender and receiver (eg. HTTP requests follows a specific format including headers and the body of message). In this project, we will implement various protocols and functionalities at the Application Layer to manage interactions between a web server and its clients. This includes tasks such as parsing HTTP requests and generating HTTP responses, handling TLS/SSL for secure communication, and implementing features such as caching, rate limiting, and load balancing to optimize server performance in order to ensure reliable and scalable service.
Some of the important protocols used in the Application layer are as follows
| Application Layer Protocols | Main Use | Applications that use the protocol |
|---|---|---|
| HTTP - Hypertext Transfer Protocol | HTTP is used for transferring web pages, images, and other resources between web servers and browsers. It defines how requests and responses are formatted and transmitted over the internet. | Web browsers such as Google Chrome, Mozilla Firefox, Safari. |
| HTTPS - HTTP Secure | The secure version of HTTP. It encrypts communication between the client (browser) and the server using protocols like TLS/SSL, ensuring secure web browsing. HTTPS is now the more common and recommended version of HTTP. | Web browsers such as Google Chrome, Mozilla Firefox, Safari. E-commerce websites like Amazon, eBay etc. |
| FTP - File Transfer Protocol | Used to transfer files between a client and a server over a network. It allows users to upload, download, or manage files on remote servers. | File transfer software like Filezilla, WinSCP |
| SMTP - Simple Mail Transfer Protocol | Used for sending emails from clients to mail servers or between mail servers. It is responsible for the outgoing email transmission. | Applications like Microsoft Outlook, Apple Mail, Gmail, etc. |
| IMAP- Internet Message Access Protocol | Used to synchronize email across all devices connected to the same email account. It allows users to access and manage their email from multiple devices while keeping the messages stored on the mail server. Any changes made, such as reading, deleting, or organizing emails, are reflected across all devices. | Applications like Microsoft Outlook, Gmail, Apple mail etc. |
| DNS - Domain Name System | Resolves domain names into IP addresses, allowing users to locate resources on the internet. It acts as a directory service, translating easily recognizable domain names into numerical IP addresses which are used to route internet traffic to the correct destination. | DNS server (eg Google public DNS ) |
| DHCP - Dynamic Host Configuration Protocol | Dynamically assigns IP addresses to devices on a network, ensuring that each device receives a unique address for communication. DHCP is responsible for automatically assigning IP addresses to devices (such as computers, smartphones, and printers) when they join a network, eliminating the need for manual configuration. | DHCP server(found in routers) |
The size of the data sent in the Application Layer can vary significantly depending on the protocol and the application being used. For HTTP requests, the minimum size can be around 20 bytes, especially for simple requests like a basic GET request. The maximum size can be several gigabytes, depending on the data being sent (e.g., file uploads or large media content). Similarly, for emails, the minimum size of an email message (such as headers) can be just a few bytes, while the maximum size is typically limited to a few megabytes.
When two application layer processes (typically on different machines or “hosts”) want to communicate over the underlying network, they must make use of the functions provided by the lower layers of the TCP/IP suite. When an application layer program is being executed on a machine, it is running as a process of the underlying operating system. These programs interact with the transport layer through the appropriate system calls provided by the OS.
Transport Layer
The Transport Layer is the software layer immediately below the Application Layer. A host (which can be a computer or any device connected to a network) may run multiple processes simultaneously. These processes could be applications such as web browsers, email clients, or servers (like web servers, file servers etc).
Each application that requires network communication must request the transport layer interface of the underlying operating system for one or more ports. A port is abstraction for a transport layer communication end point. A process that has acquired a port can use it to create several end-to-end connections to processes on other machines across the network using the Transmission Control Protocol (TCP) interface routines provided by the OS. Each such connection requires another port (and a process that has acquired the port) on the machine at the other end point. Another transport layer protocol that use the port interface is the User Datagram Protocol (UDP) which allows connectionless communication. Each port on a host machine is identified by a numeric identifier known as a port number.
In Unix/Linux systems, a process must use the socket programming interface routines to use ports. A socket is essentially a file descriptor, returned by the socket() system call. Only one port can be bound to a socket. However, more than one process may share a socket just in the same way as multiple processes can share a file descriptor in Unix/Linux (see the fork() system call). The bind() system call associates a socket to a socket address, a (IP address, port number) pair. The IP address identifies the host machine in the network - this will be discussed later. An (IP address, port number) pair uniquely determines one endpoint of a transport layer connection.
When two processes, typically running on different hosts, need to communicate with each other, each end point must create their own sockets and bind() them to (IP address, port number) pairs individually. From here, there are two possible ways to proceed. If connectionless (UDP) data transfer is initiated, then the sending process simply use the sendto() system call using the socket to transmit data to the other end. The receiving process must use the recvfrom() system call using the socket to read the data.
Application process like servers which expect data to be received from other hosts typically wait for incoming connection requests using the listen() system call, which essentially executes a “wait” for a connection request to arrive at the (IP address, Port number) corresponding to the socket. If connection oriented (TCP) data transfer is initiated, then the process that initiates the communication must use the connect() system call to send its (IP address, port number) pair to the other end requesting a connection. The connection establishment is completed once the other endpoint accepts the connection request using accept() system call.
Each connection is uniquely identified by a four-tuple, which consists of:
- IP address of the first process (source),
- Port number of the first process (source),
- IP address of the second process (destination),
- Port number of the second process (destination).
All communications between the two processes will occur through the sockets that have been created. The combination of these four values (IP address and port number for both the source and destination) uniquely identifies the communication channel between two processes. We will see more about sockets in the socket programming documentation.
A single process can bind to multiple ports. By default, a single port is assigned to a specific process at a time. However, if a process bound to a port invokes the fork() system call, the child process inherits the parent's socket descriptor, effectively sharing the same port. In such cases, both processes can operate on the same socket, which can lead to race conditions if not managed properly. In this project we would be properly dealing with the above scenario. Additionally, with the SO_REUSEADDR and SO_REUSEPORT socket options allowing for shared access and load balancing, though this requires careful management to avoid conflicts.
Port Numbers
Port numbers are represented as 16-bit unsigned integers, ranging from 0 to 65535. Ports 0-1023 (also known as reserved ports) are reserved for system services and well-known protocols. They are typically assigned to servers providing common services (for example, HTTP server uses port 80, SMTP server uses port 25 etc.).
When a computer system boots up, the OS runs initialization scripts or systemd unit files to spawn processes such as HTTP or FTP servers. Each such server uses the bind system call to acquire its designated port from the OS. Thus HTTP server (like apache) binds to port 80, SMTP server binds to port 25 and so on. The OS is responsible for ensuring that only authorized processes are allowed to bind to the reserved ports.
Ports 1024-49151 are known as registered ports. These ports are not as tightly controlled as the reserved ports (0–1023), but they can be registered with the IANA (Internet Assigned Numbers Authority) to ensure that a specific port number is reserved for a particular application or service (for example, MySQL database uses port 3306, Microsoft SQL Server uses port 1433.)
Registering ports help the developers to assign a unique port for their application, thus avoiding port conflicts. Port 8080 is widely used to run web servers locally. In the eXpServer project we will be mainly using the ports 8080, 8081, 8082, 8083.
As already stated, a process is allowed to acquire multiple ports. Hence, two processes running on two different hosts, each opening multiple ports, can transmit data between them in several (host, port) combinations. In fact, servers open multiple channels in this way for communication with a single client process. The TCP layer protocols running as part of the OS kernel ensures that the data send to a particular (host, port) combination is delivered to the correct end point. We will return to some more technical details later in this document.
Ports 49152-65535 are typically used by client applications for temporary, short lived connections. These are referred to as ephemeral ports. Generally the OS arbitrarily assigns an available port from the ephemeral port range for a client. (Binding of client socket is optional. We will see more about sockets in TCP socket programming documentation Some well known applications and port numbers are shown below in the table.
| Service, Protocol or Application | Port Number | Transport layer protocol used |
|---|---|---|
| Hypertext Transfer Protocol (HTTP) | 80 | TCP |
| HTTP Secure (HTTPS) | 443 | TCP |
| File Transfer Protocol (FTP) | 21 | TCP |
| Simple Mail Transfer Protocol (SMTP) | 25 | TCP |
| IMAP (Internet Message Access Protocol) | 143 | TCP |
| Domain Name System (DNS) | 53 | UDP |
| Dynamic Host Configuration Protocol (DHCP) | 67 | UDP |
The major protocols used in the Transport Layer include TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
TCP is a connection-oriented protocol, meaning that a connection must be established between the sending (host, port) end and receiving (host, port) end before data transmission can begin. Connection establishment is achieved through a sequence of TCP socket system calls provided by the OS . (The major system calls are listen(), connect() and accept()). The Socket Interface, play a key role in the connection setup. We will see more details about sockets and related system calls in the TCP socket programming documentation.
TCP ensures reliable, ordered, and error-checked delivery of data packets between applications on different hosts. After establishing connection, for sending data, a process must use the send() system call. The process at the receiving end of the connection must use the recv() system call to receive the data. If any TCP system call fails, then an error code indicating the cause of failure is returned. The OS provides primitives that allow the sending process to check whether the data transmitted using the send() system call is delivered to the destination. TCP guarantees that whenever data delivery is successful, it is delivered in the same sequence in which it was sent, without any transmission error.
In contrast, UDP is a connectionless protocol. It allows the transmitting (host, port) end to send a data packet to a destination (host, port) end without requiring an exclusive connection. This leads to unreliable communication. For instance a data packet could be addressed to a certain port on a host, but no process might have acquired the port. This means, the packet will be lost, but UDP provides no acknowledgement to the sending (host, port) end that a failure occurred. Failure can also occur if the data was lost during transmission. It is also possible that data is received in a different order from what was transmitted (out of order delivery). UDP is commonly used in scenarios where speed is prioritized over reliability, such as in real-time applications (e.g., video streaming or online gaming), where the loss or re-sequencing of some data does not significantly impact the overall experience. We will see more details about these protocols in the TCP Socket Programming and UDP Socket Programming documentations.
In the Transport Layer, the unit of data being transferred is called a segment. A segment consists of a header and data. The maximum size of Transport Layer segment(called Maximum Segment Size - MSS) depends on the protocol being used. The TCP header typically has a minimum size of 20 bytes and a maximum size of 60 bytes, depending on the options included in the header. On the other hand, the UDP header has a fixed size of 8 bytes. The maximum size of a TCP Transport Layer segment is generally constrained by the Maximum Transmission Unit (MTU) of the network. (The Maximum Transmission Unit (MTU) refers to the largest size of an IP packet that can be transmitted over a network link or communication channel without needing to be fragmented.) For example, in an Ethernet network with an MTU of 1500 bytes, the maximum payload for TCP is usually around 1460 bytes (1500 bytes - 20 bytes for the IP header - 20 bytes for the TCP header). If the data send by the application layer exceeds the MSS, then segmentation happens at the transport layer.
In case of UDP, there is no segmentation at the transport layer. The data send by the application layer is contained in a single UDP datagram. If the UDP datagram size exceeds the MTU, then fragmentation takes place at the network layer.
Internet Layer
In the Transport Layer, endpoints (ports) within a host are uniquely identified using port numbers. In contrast, the Internet Layer is responsible for identifying different hosts across the network. The Internet Layer uses IP addresses to uniquely identify each host within a network. An IP address (Internet Protocol address) is a unique string of “.” separated numbers (ex: 192.168.1.1) assigned to each device connected to a network that uses the Internet Protocol for communication.
In the Internet Layer (also called as Network Layer), the unit of data being transferred is called a datagram. A datagram consists of a header and a payload (the actual data). The minimum size of an IP header is 20 bytes, and the maximum size can be up to 60 bytes, depending on the presence of additional options in the header. The maximum size of an IP datagram can be as large as 65535 bytes.
The major protocols involved in the network layer include IP (Internet Protocol), ICMP (Internet Control Message Protocol) and ARP (Address Resolution Protocol). A brief introduction of these protocols are provided below.
IP (Internet Protocol) is the foundational protocol responsible for addressing, routing, and delivering packets of data across different networks. There are two versions of IP commonly used, they are IPv4 and IPv6. IPv4 is the most widely used version of the IP protocol and is based on a 32-bit address format, allowing for approximately 4.3 billion unique addresses. IPv4 address is written as four decimal numbers separated by dots (e.g., 192.168.1.2). Each set of numbers represents eight bits, or a byte, and can take a value from 0 to 255. IPv6 was introduced to address the limitations of IPv4, primarily the shortage of available IP addresses. IPv6 uses a 128-bit address format, allowing for an almost infinite number of unique addresses (approximately 340 undecillion addresses). IPv6 address is written as eight groups of four hexadecimal digits separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334) where each group represents 16 bits.
ICMP (Internet Control Message Protocol) is another internet layer protocol primarily used by hosts and routers for error reporting, network diagnostics, and management functions. Ping and Traceroute are two utilities that leverage ICMP messages: Ping is used to test connectivity between two devices, while Traceroute tracks the path packets take from source to destination by sending ICMP Echo Requests (or UDP packets), allowing the source to identify intermediate routers along the path.
Link Layer
At the bottom of the TCP/IP model is the Link layer, which deals with the physical and logical connections between devices on the same network. This layer is responsible for the reliable transfer of data over the physical medium, ensuring that devices on the same network can communicate with each other. It includes protocols such as Ethernet (for wired connections) and Wi-Fi (IEEE 802.11, for wireless connections). The Data Link layer handles the framing of data, which means encapsulating the network layer (IP) data into frames that can be transmitted over the physical network medium. It also ensures error detection and correction through mechanisms like checksums or CRC (Cyclic Redundancy Check), which help detect transmission errors and attempt to correct them at the frame level. Additionally, the Data Link layer manages access to the shared physical medium, ensuring that multiple devices on the same network can avoid collisions and interference.
ARP (Address Resolution Protocol) is the protocol that allows devices to discover each other's MAC addresses from known IP addresses. It plays a critical role in translating IP addresses (used by the Internet Layer) into MAC addresses (used by the Data Link Layer) so that data can be transmitted within a local network. A MAC address (Media Access Control address) is a unique hardware identifier assigned to a device’s network interface card (NIC). It is used to facilitate communication within a local network. Unlike IP addresses, which are logical and changeable, MAC addresses are physical identifiers embedded into the hardware by the manufacturer, ensuring device uniqueness at Data Link layer of the OSI model. A MAC address is a 48-bit address (6 bytes) represented in hexadecimal format and typically written as six groups of two hexadecimal digits separated by colons (:). The First 6 digits (00:1A:2B) of the MAC Address identify the manufacturer, called the OUI (Organizational Unique Identifier). IEEE Registration Authority Committee assigns these MAC prefixes to its registered vendors. For example, CC:46:D6 - CISCO, 3C:5A:B4 - GOOGLE, Inc etc.
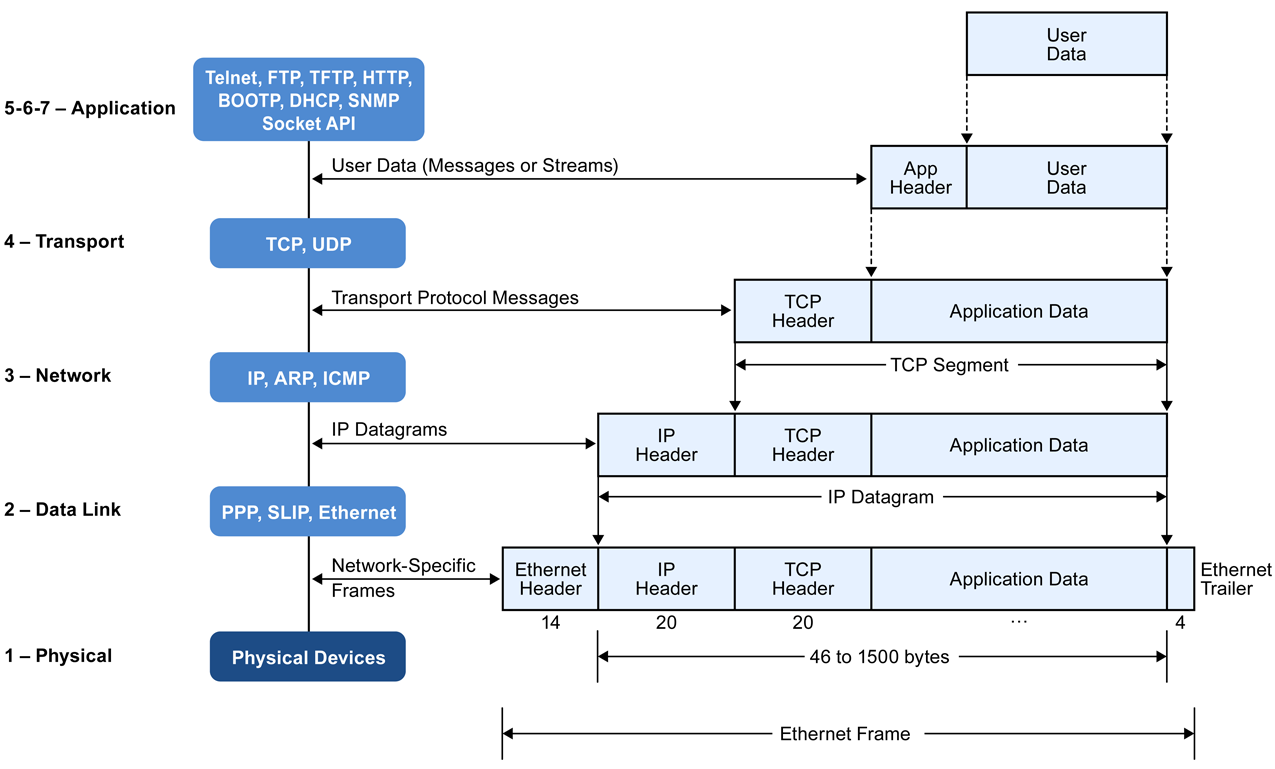
Data Flow over TCP/IP model
Now let us look into how the data flow occurs from the source to destination through different layers of the TCP/IP model.
Let’s take an example of a client(browser) requesting for a web page from the server. Here the client interacts with the application layer (user interface), i.e requesting the webpage by entering a URL. The data from the application layer now moves to the transport layer through the socket created. The transport layer then divides the data into fragments to which the TCP header is added to form TCP segment. The transport layer header contains sending and receiving port numbers along with other fields. These segments are further passed down to the Network layer, where an IP header is added to each segment to form an “IP datagram”. The IP header of each datagram contains the source and destination IP address, along with certain other fields . Subsequently, IP datagrams are passed on to the next lower layer - the Data Link layer. In the Data Link Layer, each packet is divided into one or more “frames”, and a frame header is added to each frame. The frame header includes the source and destination MAC address . This is how the data encapsulation occurs in different layers of the TCP/IP Protocol suite. Later, the physical layer sends the frame out over the network media. In between the source and the destination, the packets are passed through switches and routers. On reaching the final destination, the headers are removed sequentially at each layer(decapsulation), and finally data reaches the application layer of the destination.